Module 3 unit10 seminar post
Summary
Part A
Vendor lock-in refers to the situation where a customer becomes reliant on a specific vendor’s products or services to the extent that switching to another vendor becomes difficult or costly (Allied Market Research, 2023). Morrow et al(2021) argue that vendor lock-in issues can be related to employee expertise on one vendor verses the others. On the other hand, Opara-Martins et al (2014) identifed vendor lock-in issue to be related to many issues such as Interoperability of information between multiple cloud operators or vendors. To mitigate this, Opara-Martins et al (2014) suggest standards bodies, industry players and academia, practitioners etc. should follow the evolution or enhancements of cloud offerings with the purpose of supporting the interoperability among multiple clouds. Moreover, Opara-Martins et al (2014) argue that the Lack of Portability makes it difficult for organizations to perform migration meaning that application components can not be reused elsewhere. They mention that Cloud portability is defined can be the way to overcome vendor lock-in. Furthermore, Opara-Martins et al (2014) highlight the Lack of Standards Creates Barriers to Cloud Entry; Different cloud providers may use proprietary data formats and standards, making it difficult to transfer data seamlessly between platforms. In this case, they argue that using Standards can be regularly proposed as a way to overcome vendor lock-in.
Regarding security concerns and mitigations, below is the summary: Compliance and Legal Issues: Compliance requirements vary across industries and jurisdictions, making it challenging to make sure that cloud services comply with appropriate regulations such as GDPR, HIPAA, or PCI-DSS. This can be mitigated by carefully choosing cloud providers that offer compliance certifications and adhere to industry standards. Implement robust governance and risk management processes to ensure compliance with regulatory requirements. Additionally, conduct regular audits and assessments to identify and address compliance gaps.
Moreover, there are also concerns about possible data breaches. In this context, storing sensitive data in the cloud can expose it to the risk of unauthorized access and data breaches. This could occur due to misconfigured permissions, insider threats, or vulnerabilities in cloud services. To overcome this, the organization should encrypt data both in transit and at rest, implement access controls and authentication mechanisms, regularly audit configurations for security compliance, and employ data loss prevention (DLP) solutions to monitor and protect sensitive data (Melnick,2020).
References
Allied Market Research (2023). Cloud Native Technologies Market By Component Type, By Deployment Type, By Organizational Size, By Industry Vertical. Available from: https://www.giiresearch.com/report/amr1414790-cloud-native-technologies-market-by-component-type.html [Accessed 16 Mar. 2024]
Melnick, J. (2020). Top 6 Security Threats in Cloud Computing and How to Mitigate Them. Available from:https://blog.netwrix.com/2020/09/08/cloud-security-threats/ [Accessed 27 Feb. 2024]
Morrow, T., LaPiana, V., Faatz, D., Hueca, A. and Richmond, N., 2019. Cloud security best practices derived from mission thread analysis.
Opara-Martins, J., Sahandi, R. and Tian, F., 2014, November. Critical review of vendor lock-in and its impact on adoption of cloud computing. In International conference on information society (i-Society 2014) (pp. 92-97). IEEE.
Part B
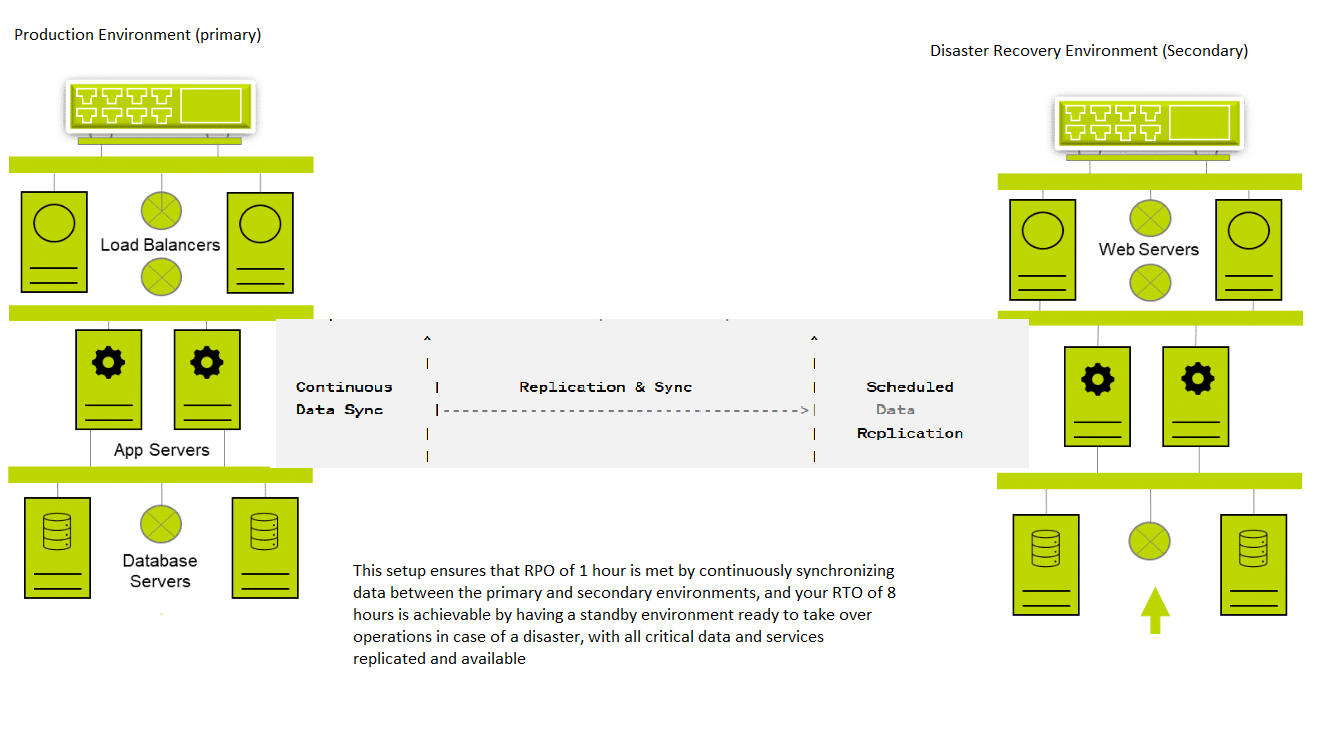
1- RPO= 1 hr; RTO= 8 hrs; high availability (HA) required.
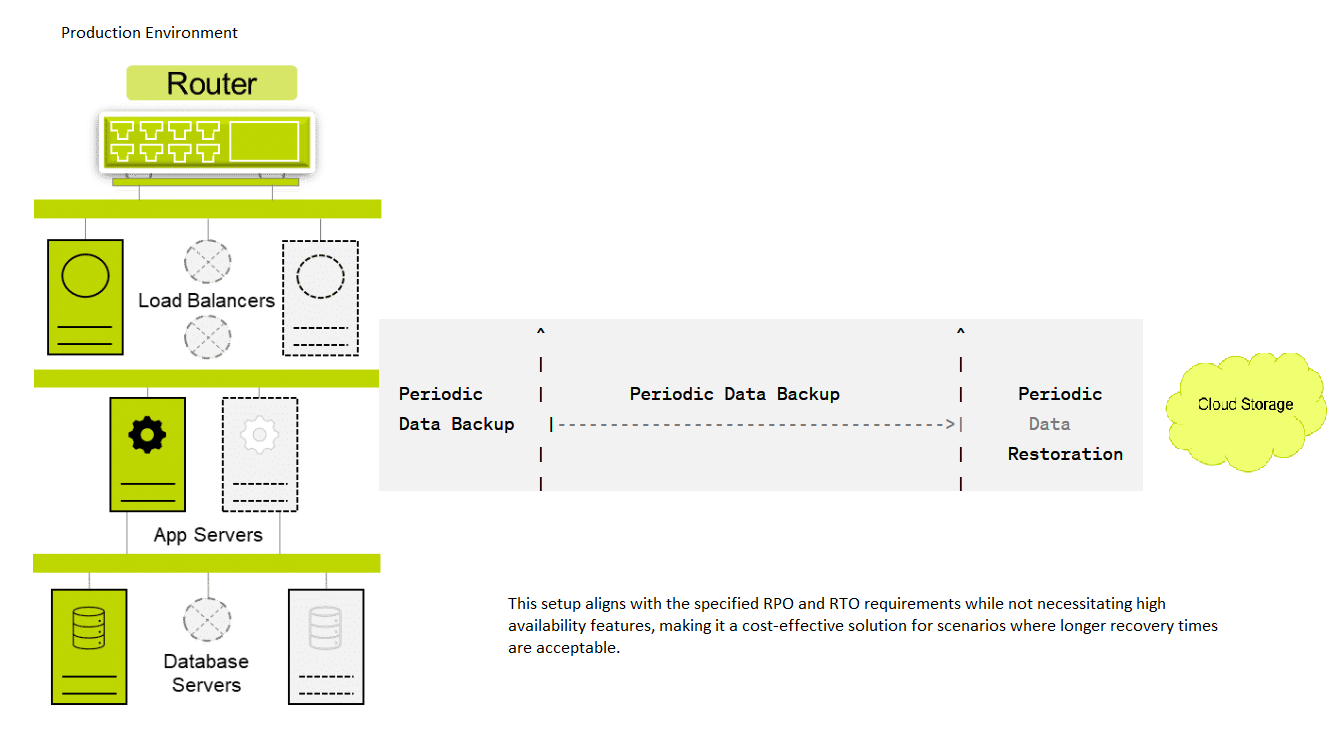
2- RPO= 24 hrs; RTO = 72 hrs; HA NOT required.
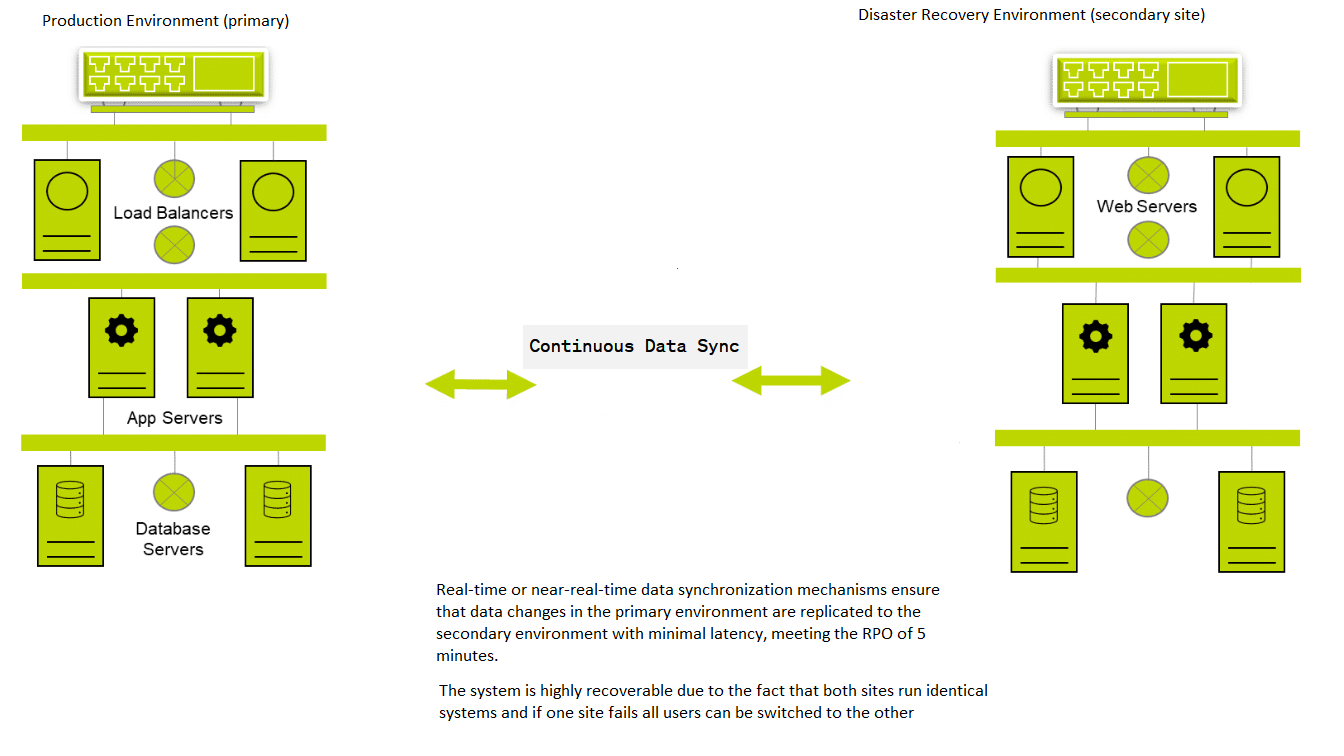
3- RPO= 5 mins; RTO= 1 hr; HA required.